Introducing Hetty: The Open-Source HTTP Toolkit Revolutionizing Security Research
In the ever-evolving landscape of cybersecurity, having the right tools can make the difference between uncovering critical vulnerabilities and leaving your systems exposed. Enter Hetty—an open-source HTTP toolkit designed specifically for security researchers, penetration testers, and bug bounty hunters. With features rivaling commercial giants like Burp Suite Pro, Hetty is quickly becoming a go-to solution for professionals seeking flexibility, power, and transparency. In this comprehensive guide, we’ll explore everything you need to know about Hetty, from its standout features to advanced usage tips, and why it deserves a spot in your security toolkit.
Why Hetty? The Rise of Open-Source Security Tools
The Need for Accessible Security Research Tools
Security research demands precision, adaptability, and the ability to dissect web traffic at scale. While proprietary tools like Burp Suite Pro dominate the market, their licensing costs and closed-source nature can limit accessibility. Hetty bridges this gap by offering a free, open-source alternative with a focus on community-driven development. Whether you're probing APIs for vulnerabilities or analyzing HTTP traffic, Hetty empowers you with enterprise-grade capabilities without the price tag.
Key Features That Set Hetty Apart
Hetty isn’t just another proxy tool—it’s a full-fledged HTTP toolkit tailored for modern security challenges. Here’s what makes it stand out:
- Machine-in-the-Middle (MITM) HTTP Proxy
Intercept, log, and analyze HTTP/HTTPS traffic with ease. Hetty’s proxy supports advanced search and filtering, making it simple to isolate critical requests. - Request/Response Interception & Modification
Pause and manipulate traffic mid-flow. Edit headers, bodies, or even cancel requests to test application resilience. - Scope Management
Organize your workflow with project-specific scopes, ensuring focused testing and clutter-free logs. - Built-In HTTP Client
Craft custom requests or replay captured traffic directly from the intuitive web interface. - Database-Backed Projects
Save sessions, logs, and configurations in a structured database for seamless continuity across tasks.
Getting Started with Hetty: Installation & Setup
Installing Hetty Across Platforms
Hetty’s cross-platform compatibility ensures it runs smoothly on macOS, Linux, Windows, and even Docker. Here’s how to get started:
macOS (Homebrew)
brew install hettysoft/tap/hetty
Linux & Windows
- Linux: Download the latest release from GitHub and add the binary to your
$PATH. - Windows: Use Scoop for hassle-free installation:
scoop bucket add hettysoft https://github.com/hettysoft/scoop-bucket.git scoop install hettysoft/hetty
Docker
Run Hetty in a container with persistent storage:
docker run -v ~/.hetty:/root/.hetty -p 8080:8080 ghcr.io/dstotijn/hetty:latest
Launching Hetty & Initial Configuration
Start Hetty with default settings:
hetty --addr :8080
This command:
- Generates a root CA certificate (
~/.hetty/hetty_cert.pem) for MITM proxying. - Initializes a BadgerDB database at
~/.hetty/hetty.dbfor project storage. - Launches the admin interface at
http://localhost:8080.
Pro Tip: Use hetty --chrome to auto-launch a preconfigured Chrome instance, bypassing certificate warnings.
Mastering Hetty’s Core Features
1. Proxy Logs & Traffic Analysis
Hetty’s proxy logs are a goldmine for dissecting web traffic. Navigate to the Proxy Logs tab to:
- Filter Requests: Use regex or keywords to pinpoint specific endpoints (e.g.,
url =~ "/api/v1"). - Copy to Sender: Right-click any log entry to clone requests into the HTTP client for replay or modification.
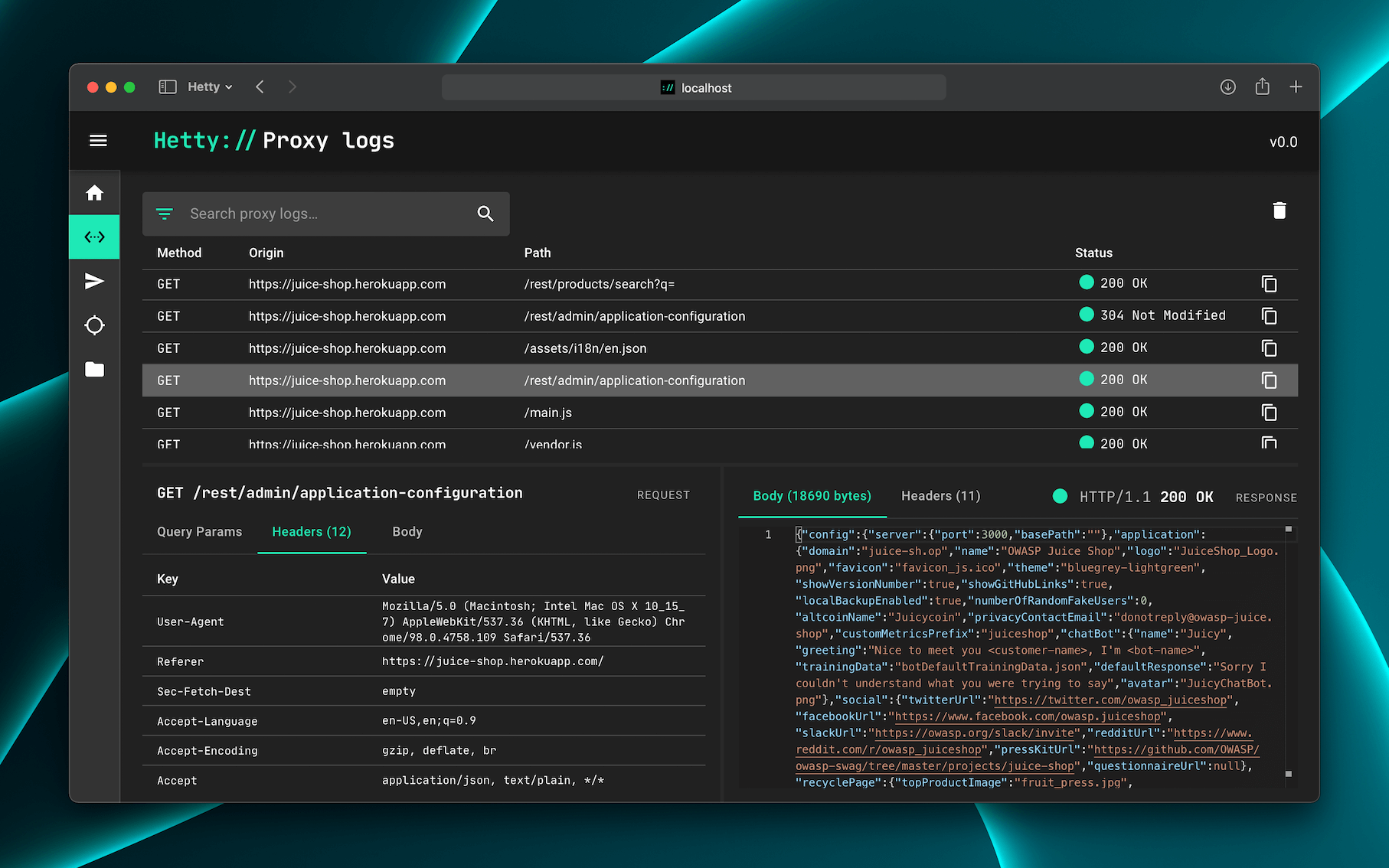
The proxy logs interface offers advanced search and one-click request cloning.
2. Intercepting & Modifying Traffic
Interception is where Hetty shines. Enable request/response interception via Project Settings:
- Request Interception: Halt outgoing requests to edit headers, bodies, or URLs.
- Response Interception: Modify server responses to test client-side handling of malformed data.
Example Workflow:
- Enable interception in your project settings.
- Trigger a request (e.g., login attempt).
- Edit the intercepted request to inject a SQLi payload.
- Forward the modified request and analyze the response.
3. Crafting Requests with the HTTP Client
The Sender module allows manual request crafting:
- Replay proxied requests with tweaked parameters.
- Test endpoints for IDOR, SSRF, or authentication flaws.
- Chain requests using variables for multi-step exploit testing.
Use Case: Simulate a broken access control attack by replaying a user’s POST request with an elevated role=admin header.
Advanced Techniques for Security Pros
Leveraging Scopes for Targeted Testing
Scopes let you define boundaries for your tests (e.g., *.example.com). Benefits include:
- Reduced Noise: Automatically exclude out-of-scope traffic.
- Focused Logs: Simplify reporting by isolating relevant requests.
Automating with Hetty’s API
For power users, Hetty’s GraphQL API (accessible at /graphql) enables automation:
- Bulk-export logs for analysis in SIEM tools like ELK.
- Integrate with CI/CD pipelines to scan staging environments pre-deployment.
Certificate Management Made Simple
Trust Hetty’s root CA system-wide to eliminate browser warnings:
hetty cert install
This command auto-configures trust stores on macOS, Linux, and Windows.
Hetty vs. Burp Suite: How They Stack Up
| Feature | Hetty | Burp Suite Pro |
|---|---|---|
| Cost | Free & Open-Source | $$$ (Subscription) |
| MITM Proxying | ✅ | ✅ |
| Interception | ✅ | ✅ |
| Scope Management | ✅ | ✅ |
| Extensibility | GraphQL API | BApp Store & Plugins |
| Community Support | Growing | Mature |
Verdict: Hetty is ideal for researchers prioritizing customization and cost-efficiency, while Burp remains the choice for enterprise teams needing plug-and-play extensibility.
Joining the Hetty Community
Contribute to the Project
Hetty thrives on community input. Whether you’re a developer, documenter, or tester, here’s how to help:
Stay Updated
- Follow @dstotijn for release announcements.
- Watch the GitHub repo to track new features like upcoming plugin support.
Conclusion: Why Hetty Belongs in Your Toolkit
Hetty represents a paradigm shift in security tooling—a fusion of open-source ethos and professional-grade functionality. Its modular design, coupled with active development, positions it as a formidable alternative to costly solutions. Whether you’re a solo researcher or part of a red team, Hetty’s flexibility and depth make it indispensable for modern web security challenges.
Ready to Dive In?
- Download Hetty from GitHub.
- Explore the official docs for advanced configurations.
- Share your journey with the community!
🔒 Secure Your Workflow with Hetty—Because Every Request Tells a Story.
Looking for more tools to elevate your security game? Check out Mobbin for design insights that can inspire your next secure app interface. From authentication flows to API dashboards, Mobbin’s repository is a treasure trove for developers and designers alike. 🚀











